Armitage organizes Metasploit's capabilities around the hacking process. There are features for discovery, access, post-exploitation, and manuver. This section describes these features at a high-level, the rest of this manual covers these capabilities in detail.
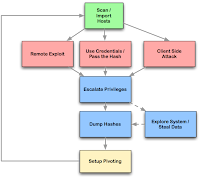
For discovery, Armitage exposes several of Metasploit's host management features. You can import hosts and launch scans to populate a database of targets. Armitage also visualizes the database of targets--you'll always know which hosts you're working with and where you have sessions.
Armitage assists with remote exploitation--providing features to automatically recommend exploits and even run active checks so you know which exploits will work. If these options fail, you can use the Hail Mary approach and unleash Armitage's smarter db_autopwn against your target database.
For those of you who are hacking post-2003, Armitage exposes the client-side features of Metasploit. You can launch browser exploits, generate malicious files, and create Meterpreter executables.
Once you're in, Armitage provides several post-exploitation tools built on the capabilities of the Meterpreter agent. With the click of a menu you will escalate your privileges, dump password hashes to a local credentials database, browse the file system like you're local, and launch command shells.
Finally, Armitage aids the process of setting up pivots, a capability that lets you use compromised hosts as a platform for attacking other hosts and further investigating the target network. Armitage also exposes Metasploit's SOCKS proxy module which allows external tools to take advantage of these pivots. With these tools, you can further explore and maneuver through the network.
The rest of this manual is organized around this process, providing what you need to know in the order you'll need it.
1.2 Necessary Vocabulary
To use Armitage, it helps to understand Metasploit. Here are a few things you absolutely must know before continuing:Metasploit is a console driven application. Anything you do in Armitage is translated into a command Metasploit understands. You can bypass Armitage and type commands yourself (covered later). If you're ever lost in a console, type help and hit enter.
Metasploit presents its capabilities as modules. Every scanner, exploit, and even payload is available as a module. If you're scanning a host, you use an auxiliary module. Before launching a module, you must set one or more variables to configure the module. The exploit process is similar. To launch an exploit, you must choose an exploit module, set one or more variables, and launch it. Armitage aims to make this process easier for you.
If you successfully exploit a host, you will have a session on that host. Armitage knows how to interact with shell and Windows meterpreter sessions.
Meterpreter is an advanced agent that makes a lot of post-exploitation functionality available to you. Armitage is built to take advantage of Meterpreter. Working with Meterpreter is covered later.
The Metasploit Unleashed course maintained by the Offensive Security folks is excellent. I recommend reading it before going further.
2.1 Getting Started: Linux
Metasploit has an RPC daemon that can accept local and remote connections. To start the Metasploit RPC daemon:
cd /pentest/exploits/framework3
./msfrpcd -f -U msf -P test -t Basic
This will start msfrpcd with the user msf, password test, SSL listener, on the default port 55553.
Optionally, you can use the Start MSF button to launch Metasploit for you. You'll still need to enter your database information. I recommend launching the Metasploit daemon separately though. If something happens to Armitage, you can reconnect to the Metasploit RPC daemon and all of your sessions and information will still be there.
If you have BackTrack R42, use the MySQL database. It's already configured. Start it with:
/etc/init.d/mysql start
Then use root as the username, toor as the password, 127.0.0.1 as your host, and any name you choose as your database name.
You should not use the SQLite database with Armitage.
Once you have a database, navigate to the folder containing the Armitage files and type:
./armitage
Make sure you check the Use SSL box when connecting.
2.2 Getting Started: Windows
To install Armitage on Windows (video):
- Download and Install the Metasploit Framework from http://www.metasploit.com/.
- Get the package with all of the dependencies.
- Go to Start -> All Programs -> Metasploit Framework -> Metasploit Update
- Unzip the Armitage archive into the Metasploit install directory (e.g., c:\program files\rapid7\framework)
- Create a desktop shortcut to [metasploit folder]\armitage.bat and set the icon to [metasploit folder]\icons\armitage.ico
Unzipping the Armitage Windows archive over your framework install will add files that tell Armitage where to find Metasploit's database settings and how to start the RPC daemon. You only need to go through this process once. To update Armitage go to Start -> Programs -> Metasploit 3 -> msfupdate. If you see an error stating a conflict with any of the existing Armitage files, delete them, and update Metasploit again.
To use Armitage:
- Double-click the shortcut. Click Start MSF and wait for a connection.
If something goes wrong, press Ctrl-Alt-Del and kill any ruby processes that you see.
2.4 Getting Started: MacOS X
Armitage works on MacOS X but it's not a supported platform for Armitage. Metasploit does not have an official package for OS X. There is a lot of manual setup involved getting the pre-requisites working.
I put a lot of energy into Armitage and supporting Windows takes a lot out of me as it is. I'm happy to fix MacOS X specific bugs in Armitage but I will not help you troubleshoot your Metasploit or database installation on MacOS X. I'm not withholding the secret from you--I do not use Metasploit on MacOS X and I have no idea how to help you.
Armitage on MacOS X works fine as a remote client to Metasploit. Download the Linux package, extract it, and double-click the armitage.jar file to get started.
3. User Interface Tour
3.1 Overview
The Armitage user interface has three main panels: modules, targets, and tabs. You may click the area between these panels to resize them to your liking.

3.2 Modules
The modules panel lets you launch a Metasploit auxiliary module, throw an exploit, generate a payload, and even run a post-exploitation script. Click through the tree to find the desired module. Double click the module to bring up a dialog with options.
Armitage will place highlighted hosts from the targets panel into the RHOSTS variable of any module launched from here.
You can search for modules too. Click in the search box below the tree, type a wildcard expression (e.g., ssh_*), and hit enter. The module tree will then show your search results, already expanded for quick viewing. Clear the search box and press enter to restore the module tree to its original state.
3.3 Targets - Graph View
The targets panel shows all hosts in the current workspace. Armitage represents each target as a computer with its IP address and other information about it below the computer. The computer screen shows the operating system the computer is running.

A red computer with electrical jolts indicates a compromised host. Right click the computer to use any sessions related to the host.
A directional green line indicates a pivot from one host to another. Pivoting allows Metasploit to route attacks and scans through intermediate hosts. A bright green line indicates the pivot communication path is in use.
Click a host to select it. You may select multiple hosts by clicking and dragging a box over the desired hosts. Where possible, Armitage will try to apply an action (e.g., launching an exploit) to all selected hosts.
Right click a host to bring up a menu with available options. The attached menu will show attack and login options, menus for existing sessions, and options to edit the host information.
The login menu is only available after a port scan reveals open ports that Metasploit can log in to. The Attack menu is only available after finding attacks through the Attacks menu bar. Shell and Meterpreter menus only show up when a shell or Meterpreter session exists on the selected host.
Several keyboard shortcuts are available in the targets panel. You may edit these in the Armitage -> Preferences menu.
* Ctrl Plus - zoom in
* Ctrl Minus - zoom out
* Ctrl 0 - reset the zoom level
* Ctrl A - select all hosts
* Escape - clear selection
* Ctrl C - arrange hosts into a circle
* Ctrl S - arrange hosts into a stack
* Ctrl H - arrange hosts into a hierarchy. This only works when a pivot is set up.
* Ctrl R - refresh hosts from the database
* Ctrl P - export hosts into an image
Right click the targets area with no selected hosts to configure the layout and zoom-level of the targets area.
3.4 Targets - Table View
If you have a lot of hosts, the graph view becomes difficult to work with. For this situation Armitage has a table view. Go to View -> Targets -> Table View to switch to this mode. Armitage will remember your preference.

Click any of the table headers to sort the hosts. Highlight a row and right-click it to bring up a menu with options for that host.
Armitage will bold the IP address of any host with sessions. If a pivot is in use, Armitage will make it bold as well.
3.5 Tabs
All functionality in Armitage is made available below the targets and module area. Each panel you open is presented in its own tab. This is where you will spend most of your time when working with Armitage. There are several panels.
3.6 Consoles
A console panel lets you interact with a command line interface through Armitage. The Metasploit console, Meterpreter console, and shell session interfaces all use a console panel.
The console panel features a command history. Use the up arrow to cycle through previously typed commands. The down arrow moves back to the last command you typed.
In the Metasploit console, use the Tab key to complete commands and parameters. This works just like the Metasploit console outside of Armitage.
Use Ctrl Plus to make the console font size larger, Ctrl Minus to make it smaller, and Ctrl 0 to reset it. This change is local to the current console only. Visit Armitage -> Preferences to permanently change the font.
Press Ctrl F to show a panel that will let you search for text within the console.
Use Ctrl A to select all text in the console's buffer.
Armitage sends a use or a set PAYLOAD command if you click a module or a payload name in a console.
4. Host Management
4.1 Workspaces
Use the Hosts menu to add hosts to Metasploit's database. Hosts added to Metasploit are kept in workspaces. A workspace is like a separate database. Workspaces allow you to organize hosts into groups and switch between them.
Use the Workspaces menu to create, switch, and remove workspaces.
4.2 Importing Hosts
To add host information to Metasploit, you can import it. Metasploit lets you import Nessus scans, NMap output, and more. The Hosts -> Import Hosts menu exposes this capability to you.
You may add hosts one IP address at a time through Hosts -> Add Hosts...
4.3 NMap Scans
You may also launch an NMap scan from Armitage and automatically import the results into Metasploit. The Hosts -> NMap Scan menu has several scanning options.
NMap's output is available in the window you launched Metasploit's RPC daemon from. If you launched Metasploit's RPC daemon from Armitage (the button), then go to View -> RPC Console to watch NMap's output.
Whether you import an NMap scan or launch it from Armitage, Armitage will update the hosts database with the operating system information provided by NMap.
NMap scans do not take advantage of pivots you have set up.
I recommend running your NMap scans externally and importing the results into Armitage. Some scans take a long time and Armitage is unable to give you a progress report for the scan. Use nmap [options] -oX whatever.xml to create a whatever.xml file for importing.
4.4 MSF Scans
Metasploit has many modules for scanning and fingerprinting hosts. These modules work quite well and result in accurate fingerprints when common services are available.
Armitage makes it easy to launch many of these at once through the Hosts -> MSF Scans menu item. Click this item, type in a range of IP addresses, and watch the magic happen.
Armitage uses all auxiliary modules that fingerprint a service. Type _version into the Module search box and hit enter to see a list of these modules.
You can watch the progress of an MSF Scan through View -> Jobs
5. Exploitation
5.1 Remote Exploits
Before you can attack, you must choose your weapon. Armitage makes this process easy. Use Attacks -> Find Attacks to generate a custom Attack menu for each host. This process uses Metasploit's db_autopwn feature to recommend the best exploits on a host by host basis. Use the by vulnerability option only if you've imported a vulnerability scan.
You can exploit a host by right-clicking it, selecting Attack, and choosing an exploit. To show the most appropriate attacks, make sure the operating system is set for the host. The Attack menu is limited to exploits with a rating of great or excellent.
Some useful exploits (e.g., lsass) are ranked good and they don't show in the attack menu. You can still launch them using the modules panel. Highlight the host (or hosts) that you want to exploit and navigate to the desired exploit in the modules panel. Double click the exploit and you will see the launch dialog.
Under Armitage -> Preferences there is an option to change the minimal exploit ranking. Try good or normal if you want more exploits in the Attack menu.
5.2 Which exploit?
Learning which exploits to use and when comes with experience. Some exploits in Metasploit implement a check function. These check functions connect to a host and check if the exploit applies. Armitage can use these check functions to help you choose the right exploit when there are many options. For example, targets listening on port 80 will show several web application exploits after you use Find Attacks. Click the Check exploits... menu to run the check command against each of these. Once all the checks are complete, press Ctrl F and search for vulnerable. This will lead you to the right exploit.

Clicking a host and selecting Services is another way to find an exploit. If you have NMap scan results, look at the information field and guess which server software is in use. Use the modules panel to search for any Metasploit modules related to that software. One module may help you find information required by another exploit. Apache Tomcat is an example of this. The tomcat_mgr_login module will search for a username and password that you can use. Once you have this, you can launch the tomcat_mgr_deploy exploit to get a shell on the host.
If all this fails, you have the hail mary option. Attacks -> Hail Mary launches this feature. Armitage's hail mary option is a smarter db_autopwn. It first finds exploits relevant to your target set. It then filters these exploits using known information about the targets. For example, Hail Mary won't launch a Linux exploit against a Windows target. These exploits are then sorted so the best ones are launched first. Once this preparation is complete, Armitage launches these exploits against your targets. This feature won't give you every possible shell, but it's a good option if you don't know what else to do.
5.3 Launching Exploits
Armitage uses this dialog to launch exploits:

The exploit launch dialog lets you configure variables for a module and choose whether to use a reverse connect payload.
Variables are presented in a table. Double click a value to edit it. If a variable requires a filename, double click the variable name to bring up a file chooser dialog. You may also view and set advanced options by checking Show advanced options.
Armitage chooses a payload for you. Windows exploits will use a Meterpreter payload. UNIX exploits will launch a command shell.
Click Launch to launch the exploit. If the exploit is successful, the host's computer will change color in the targets panel. Metasploit will also print a message to any open consoles.
5.4 Client-side Exploits
Armitage makes it easy to configure client-side exploits available with Metasploit. The Attacks menu has options to set up browser attacks, email client attacks, and even generate malicious files.
Attacks set up in this way are pre-configured to connect back to your current Metasploit instance. The exploit handler is already configured for you.
Browser Autopwn creates a URL that uses JavaScript to fingerprint anyone who connects and launches an appropriate browser exploit against them.
File Autopwn sets up a URL serving many malicious files, generated for your viewing pleasure. Visit the URL, download a file, and send it to your target. Or get them to download it directly.
Hosts compromised via client-side exploits will show up in the targets panel when they connect back. Armitage does not need to know about these hosts beforehand.
5.5 Generate a Payload
Exploits are great, but don't ignore the simple stuff. If you can get a target to run a program, then all you need is an executable. Armitage can help you generate an executable from any of Metasploit's payloads. Choose a payload in the modules panel, double click it, select the type of output, and set your options. Once you click launch, a save dialog will ask you where to save the file to.

When you generate a payload, you're responsible for setting up a listener to interact with it. Select the multi/handler output type in the payload dialog to set up a handler for the payload with your desired options.
For Meterpreter and shell payloads, you may also go to Armitage -> Listeners and choose a bind listener to connect to a listening payload or a reverse listener to wait for a payload to connect.
6. Post Exploitation
6.1 Managing Sessions
Armitage makes it easy to manage the Windows Meterpreter agent once you successfully exploit a host. Hosts running the Meterpreter payload will have a Meterpreter N menu for each Meterpreter session.

If you have shell access to a host, you will see a Shell N menu for each shell session. Right click the host to access this menu. If you have a Windows shell session, you may go to Shell N -> Meterpreter... to upgrade the session to a Meterpreter session. If you have a UNIX shell, go to Shell N -> Upload to upload a file using the UNIX printf command.
6.2 Access
Once you exploit a host, duplicating your access should be a first priority. Meterpreter N -> Access -> Duplicate will generate a meterpreter executable, upload, and run it on the host for you. If you lose the original session, this will give you a fall back.
Some exploits result in administrative access to the host. Other times, you need to escalate privileges yourself. To do this, use the Meterpreter N -> Access -> Escalate Privileges option to try several Windows privilege escalation options.
6.3 File Browser
Meterpreter gives you several options for exploring a host once you've exploited it. One of them is the file browser. This tool will let you upload, download, and delete files.
Right-click a file to download or delete it. If you want to delete a directory, make sure it's empty first.
If you have system privileges, you may modify the file timestamps using the File Browser. Right-click a file or directory and go to the Timestomp menu. This features works like a clipboard. Use Get MACE Values to capture the timestamps of the current file. Right-click another file and use Set MACE Values to update the timestamps of that file.
Go to Meterpreter N -> Explore -> Browse Files to access the File Browser.
6.4 Command Shell
You can reach a command shell for a host through Meterpreter N -> Interact -> Command Shell. The Meterpreter shell is also available under the same parent menu.
Navigating to the Meterpreter N menu for each action gets old fast. Right-click inside the Meterpreter shell window to see the Meterpreter N menu items right away.
Close the command shell tab to kill the process associated with the command shell.
6.5 Post-exploitation Modules
Metasploit has several post-exploitation modules too. Navigate the post branch in the module browser. Double-click a module and Armitage will show a launch dialog. Armitage will populate the module's SESSION variable if a compromised host is highlighted. Each post-exploitation module will execute in its own tab and present its output to you there.
7. Maneuvering
7.1 Pivoting
Metasploit can launch attacks from a compromised host and receive sessions on the same host. This ability is called pivoting.
To create a pivot, go to Meterpreter N -> Pivoting -> Setup.... A dialog will ask you to choose which subnet you want to pivot through the session.
Once you've set up pivoting, Armitage will draw a green line from the pivot host to all targets reachable by the pivot you created. The line will become bright green when the pivot is in use.
To use a pivot host for a reverse connection, set the LHOST variable in the exploit launch dialog to the IP address of the pivot host.
7.2 Scanning and Browsing
Once you've owned a host, it's good to explore and see what else is on the same network. If you've set up pivoting, Metasploit will tunnel TCP connections to eligible hosts through the pivot host. These connections must come from Metasploit though.
Use the MSF Scans (Hosts -> MSF Scans) to launch scans that will honor the pivots you've setup.
You may also set up a SOCKS proxy to let other tools take advantage of the pivots you've setup. Go to Armitage -> SOCKS Proxy... to launch the SOCKS proxy server.
7.3 Pass-the-Hash
When you login to a Windows host, your password is hashed and compared to a stored hash of your password. If they match, you're in. When you attempt to access a resource on the same Windows domain, the stored hash is sent to the other host and used to authenticate you. With access to these hashes, you can use this mechanism to take over other hosts on the same domain. This is called a pass-the-hash attack.
To collect hashes, visit Meterpreter N -> Access -> Dump Hashes. You need administrative privileges to do this. Armitage will store the collected hashes in a database for your use later.
You may view collected hashes through View -> Credentials. For your cracking pleasure, the Export button in this tab will export credentials in pwdump format.
To install Meterpreter on another Windows host, right-click the host and go to Attack -> smb -> Pass the Hash.... This will present a dialog where you can select which hash to login with.
Your hosts must be on the same active directory domain for this attack to work.
7.4 Netcat Listeners
A popular technique for creating a quick backdoor is to use netcat to launch a command shell on connection. Netcat can either listen for a connection or connect back to you.
Armitage can take advantage of these sessions. Go to Armitage -> Listeners and choose bind to connect to a listening netcat session. Choose reverse to wait for netcat to connect back to you. This is one way to receive a shell from a friend who has already compromised a host.
7.5 Password Brute Force
Metasploit can attempt to guess a username and password for a service for you. This capability is easy to use through the modules panel.
Metasploit supports brute forcing through the auxiliary modules named service_login. Type login in the modules panel to search for them.
To brute force a username and password over SSH, browse to auxiliary/scanner/ssh/ssh_login in the modules panel and double click it.
If you know the username, set the USERNAME variable. If you'd like Metasploit to brute force the username, select a value for USER_FILE. Double click the USER_FILE variable to bring up a file chooser where you can select a text file containing a list of usernames.
Metasploit has many files related to brute forcing in the [metasploit install]/data/wordlists directory.
Set the PASS_FILE variable to a text file containing a list of passwords to try.
If you're only brute forcing one host and you have a lot of usernames/passwords to try, I recommend using an external tool like Hydra. Metasploit does not make several parallel connections to a single host to speed up the process. This lesson can be taken one step further--use the right tool for each job.
8. Remote Metasploit
8.1 Remote Connections
You can use Armitage to connect to an existing Metasploit instance on another host. Working with a remote Metasploit instance is similar to working with a local instance. Some Armitage features require read and write access to local files to work. Armitage removes or degrades these features when managing a naked remote Metasploit instance.
Simply specify the remote IP address, remote port, RPC username, and RPC passowrd in Armitage's starting dialog and click Connect. You do not need to specify database settings if the database is already configured in the running Metasploit instance.
Do not connect multiple clients to Metasploit unless you use Armitage's network attack server feature.
8.2 Launching the RPC Server from the Metasploit Console
Armitage connects to Metasploit's RPC server. You can launch Metasploit's RPC server as described in the Getting Started: Linux section. It's also possible to connect Armitage to a running Metasploit console.
In the Metsploit console, type:
load xmlrpc
Optionally, you can specify the host and port to bind to with:
load xmlrpc ServerHost=address ServerPort=port
Take note of the RPC username and password. You will need these when you launch Armitage.

Once the RPC server is loaded you can connect Armitage to it. Make sure Use SSL is not checked.
This process works on Windows and Linux.
When emulating a social engineering attack or using client-side exploits, it's helpful to set up Metasploit on a remote server to receive sessions. I configure my listeners through Metasploit's console and connect with Armitage to manage the post-exploitation process.
8.3 Multi-Player Metasploit
Use Armitage's network attack server mode to collaborate using Metasploit. First, you must start a Metasploit RPC instance. Then, on the same system, run Armitage's network attack server software:
java -jar armitage.jar --server host port user password ssl?
Or:
./armitage --server host port user password ssl?
Armitage's network attack server will connect to Metasploit on the specified port with the username and password you provide. Use 1 for ssl? if you'd like Armitage to connect to Metasploit using SSL. Leave this value empty otherwise. For the host value, specify the IP address remote Armitage users will use to connect to your Metasploit instance.
Make sure you specify the remote IP address of the host and not 127.0.0.1. Armitage's network attack server sets a Metasploit global variable to tell clients how to connect to it.
This server adds extra features to Armitage clients connecting to Metasploit remotely. Most of the features degraded during a remote connection are now present.
Multiple users can now connect to one Metasploit instance and collaborate with each other. Host information, scan data, and sessions are shared using Metasploit's database.

View -> Event Log lets you communicate with users connected to the same Metasploit instance.
Multiple users can now use any Meterpreter session at the same time. Each user can open one or more command shells, browse files, and take screenshots of the compromised host.
Metasploit shell sessions are automatically locked and unlocked when in use. If a user is interacting with a shell, Armitage will warn you that it's in use.
The file browser download feature will still download to the remote server. Use a persistent sftp connection to files downloaded through Meterpreter. The file browser upload feature will upload your file to the Metasploit system first and then upload it to the target host.
Penetration testers will find this feature invaluable. Imagine you're working on a pen test and come across a system you don't know much about. You can reach back to your company and ask your local expert to load Armitage and connect to the same Metasploit instance. They will immediately have access to your scan data and they can interact with your existing sessions... seamlessly.Or, imagine that you're simulating a phishing attack and you get access to a host. Your whole team can now work on the same host. One person can search for data, another can set up a pivot and search for internal hosts to attack, and another can work on persistence. The sky is the limit here.





 9:21 AM
9:21 AM
 secure your world
secure your world






 Posted in:
Posted in: 

